Advent of Cyber 2025 – Day 5 Walkthrough
This challenge is all about Insecure Direct Object Reference, or IDOR, which is one of the easiest web application vulnerabilities to learn to identify, and is often recommended as a good starting point for bug bounty hunters.
OWASP publishes a great reference for IDOR testing.
I skipped the first two questions, which ask ‘what IDOR stands for’ and ‘what type of privesc does IDOR typically represent’ – as you can easily read the text or Google them.
Question 3
Exploiting the IDOR found in the view_accounts parameter, what is the user_id of the parent that has 10 children?
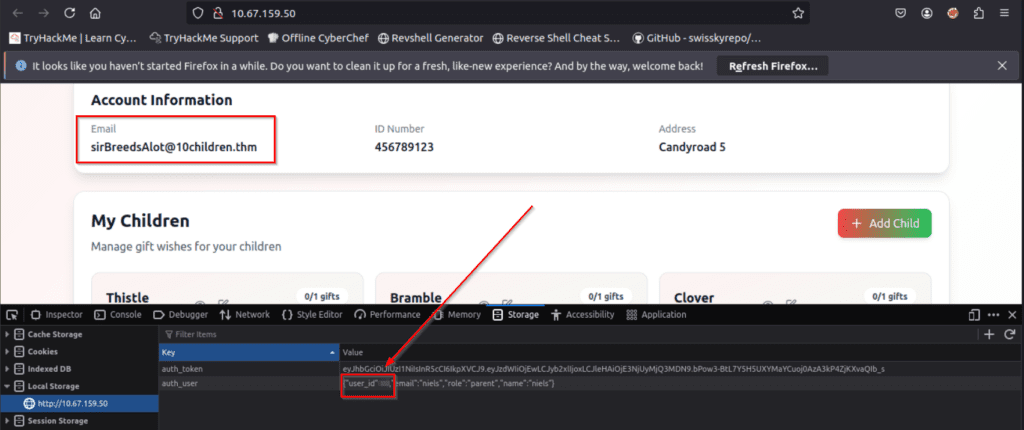
We need to manually iterate through numerical values of the ‘user_id’ parameter until we find the user with 10 children.
To do so, right click and use the inspection tool, then select the Storage tab. On the left, select the IP address corresponding with the target and look for the ‘user_id’ parameter as shown below. Double click on it to edit, then refresh the page.
TryHackMe does give us a starting point – our own (niels) user has a user_id of ’10’, and we can see in the answer form that the answer has two digits. So – that leaves only 89 entries to try! Luckily, whoever made this challenge isn’t so cruel as to put it that high up – just start with 11 and continue to iterate one digit at a time.
Answer Hint:
Make sure you’re editing the correct parameter. Keep in mind – in a real web app pentest, we would want to test all of the parameters for IDOR vulnerabilities!
