The Top Cybersecurity Threats Facing Small Businesses Today
The more we know about our attackers, the better we’ll be able to defend our small businesses against them. Small businesses share many of the same threats as large organizations, but operate under different constraints—as well as some unique advantages.
For example, phishing and business email compromise (BEC) represent two of the most common (and constant) threats to businesses both large and small.
It is true that the worlds best hacker organizations – highly skilled groups of threat actors known as Advanced Persistent Threats (APTs) — often backed by nation-states — are less likely to target small businesses primarily, since the return on investment for their skill and resource levels may be considered too low.
But that doesn’t mean small businesses are safe. In fact, the opposite is true. The combination of having weaker defenses, along with facing many of the same threats as large corporations, means that the overall risk facing small businesses is actually greater than the cyber risk for big companies.
In this article, we’ll take a look at the risks facing small businesses today. First, we’ll take a quick look at why small business get targeted in the first place. Then, we’ll cover the top three threats that businesses find themselves contending with everyday – whether they know it or not. For each of the top three threats, we’ll take a look at some of the most important mitigations for that threat. There’s a lot of overlap but one of the goals is to create a layered defense capable of allowing you to prevent, detect, and respond to modern threats.
Why Small Businesses Are Prime Targets
Attackers often target small businesses for various reasons. Click on each bullet to learn more about common challenges and solutions!
Small businesses typically have weak defenses.
Most small businesses lack dedicated security personnel or formal processes for managing risk—and most still rely on traditional antivirus (AV) software as their primary line of defense.
There are many ways to improve your security posture, but the biggest problem is that antivirus (AV) alone isn’t nearly enough. Even premium AV products are surprisingly easy for skilled attackers to bypass. In fact, extensive testing shows that paid solutions offer little advantage over free ones when it comes to detecting modern threats.
That’s why we strongly advocate for Managed Detection and Response (MDR). Unlike traditional AV, MDR collects extensive telemetry (data) from your devices and routes it to a real, human-staffed Security Operations Center (SOC – pronounced ‘sock’). Inside a SOC, security analysts and other cybersecurity experts continuously monitor for suspicious behavior, investigate alerts, and respond to active threats in real time.
MDR is not just a tool—it’s a service layer backed by expert oversight. That’s why we recommend saving your money by skipping premium AV—and investing instead in MDR.
We consider MDR to be one of the most valuable protections a small business can have—and it’s a cornerstone of our Security Essentials™ package.
Small businesses aren’t just targeted for their own data—they’re often a means to a bigger end.
Attackers frequently exploit small businesses as entry points into larger organizations they work with. This can include suppliers, vendors, or clients in more lucrative industries. In many cases, a small business is part of a larger supply chain or has access—directly or indirectly—to valuable systems and information.
Even something as simple as compromised email access can be weaponized. If an attacker gains control of a small business’s inbox, they can launch convincing phishing campaigns against partners, customers, or suppliers.
In other words, even if your business isn’t the end target, you might still be a great target en route to attacking more lucrative victims.
Small businesses often underestimate their own value to attackers.
Many small businesses assume they’re not valuable enough to be targeted—especially if they don’t handle sensitive data like credit card numbers or medical records. But that’s a dangerous misconception.
Attackers can still profit from you in several ways:
- Deploying ransomware to extort payment for access to your own systems and data
- Stealing intellectual property, proprietary processes, or internal documentation
- Reselling access to your computers, network, email accounts, or endpoints on dark web markets
In today’s cybercrime economy, every part of the attack lifecycle is monetized. Access brokers sell initial footholds to ransomware groups. Malware developers lease their tools in exchange for a cut of the profits. Even relatively unsophisticated attackers can make money by compromising small business systems and flipping access to more skilled threat actors.
The bottom line? If you have computers, credentials, or connectivity—you’re worth targeting.
The Top 3 Cyber Threats Facing Small Businesses
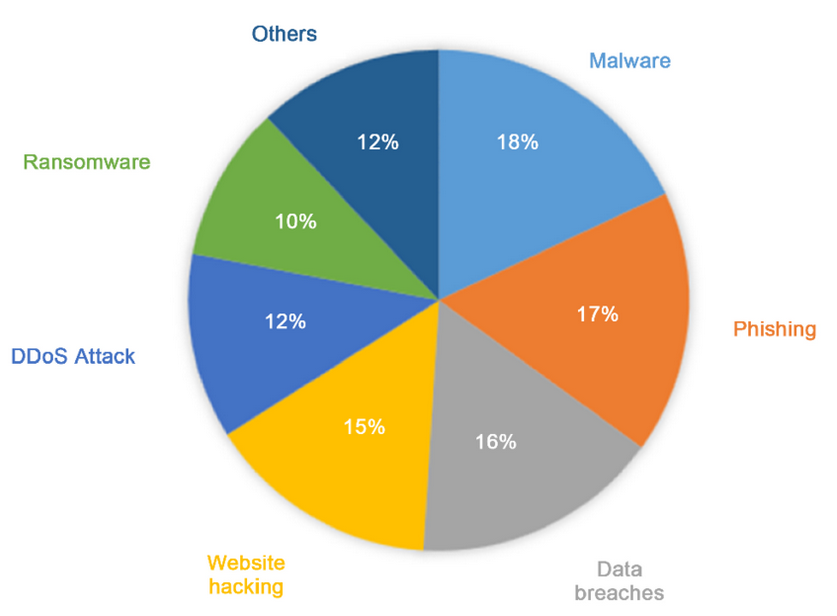
Let’s break down the three most common types of threats that small businesses face, along with how to defend against them:
- Phishing and Business Email Compromise (BEC)
- Ransomware and Ransom-Based Attacks
- Insider Threats
#1 – Phishing and Business Email Compromise (BEC)
Phishing and Business Email Compromise are two of the most common types of attacks and share many similarities. Let’s start with phishing, one of the most widespread and effective cyber threats.
Phishing is an attack in which the attacker(s) send deceptive emails designed to trick employees into clicking malicious links, entering login credentials, or downloading malware. Modern phishing attacks are becoming increasingly sophisticated. Attackers do their homework to make their attacks more credible, and they leverage a variety of techniques to prevent their fraudulent emails from raising flags.
Business Email Compromise (BEC) is a more targeted variant of phishing in which an attacker impersonates a trusted contact—such as a CEO, coworker, or vendor — often to request wire transfers or sensitive information.
Both phishing and BEC rely on social engineering: manipulating human behavior to bypass technical defenses. Attackers often create a false sense of urgency and exploit publicly available information to increase credibility. For example, they might pose as a manager and send a last-minute request near the end of the workday—when critical thinking is low and quick compliance is more likely.
How to Defend Against Phishing and Business Email Compromise (BEC)
Defending against phishing and BEC requires a multi-layered defense, combining people, processes, and technology.
- Managed Detection and Response (MDR):
Our top recommendation. Managed Detection and Response, or MDR, provides real-time threat monitoring and response, and can detect the signs of a successful phishing or BEC attack at every stage in the attack chain. This detection capability often prevents an incident from becoming a full-blown breach. Since MDR also relies on a human led Security Operations Center (SOC), it’s like having a team of cybersecurity experts watching over your devices and network. - Advanced Email Security Tools:
Integrated email protection solutions (like Proofpoint, Microsoft Defender for Office 365, or Google Workspace Enterprise protections) scan for phishing attempts, malicious links, spoofed domains, and suspicious behavior. While not foolproof, they’re a valuable first layer of defense—and in our testing, they’re the second-most effective technical control. - Harden Your Systems:
Throughout this course, we’ll cover many different techniques and tools to help you tighten up security and improve your security posture. While hardening your systems may not directly prevent or detect email-based attacks, it will help make it much more difficult for attackers to achieve their objectives. For example, using strong and unique passwords will help prevent an attacker from gaining access to other systems or escalate their privileges. Deploying the Principle of Least Privilege (PoLP) will ensure that even if an attacker successfully phishes you or an employee, they will only gain access to a low-privileged account. There are many other examples, and this course will help guide you through the most important steps to take. - User Awareness Training:
No matter how good your tech stack is, people are still your frontline. Regular training helps employees spot red flags and understand how to respond when something feels off.
#2 – Ransomware and Ransom-Based / Extortion Attacks
Ransomware is a type of malware that encrypts your files and demands payment—usually in cryptocurrency—to restore access. While some ransomware groups target large enterprises, many go after small businesses, who may be more likely to pay out of desperation due to the immediate operational impact.
What makes ransomware especially dangerous is its ability to bring your business to a grinding halt. Encrypted customer records, financial data, and operational files can mean days or even weeks of downtime—resulting in lost revenue, reputational harm, and expensive recovery efforts.
But ransomware isn’t the only extortion tactic attackers use.
Some cybercriminals exfiltrate (steal) sensitive data before encrypting it, threatening to leak or sell the data if the ransom isn’t paid—a tactic known as double extortion. Others may skip the encryption entirely and go straight to blackmail, especially if they gain access to emails, customer data, or private business documents. Double extortion attacks are particularly effective against business that house a lot of sensitive data, like companies in the medical, legal, and financial industries.
Another interesting example is that of ransoming account access. Sometimes attackers will simply gain access to an account (for example, a Facebook business account), change the password, and then hold the account for ransom. Some micro-businesses that rely entirely on Facebook accounts have seen their business destroyed because the account held all of the information they need for their business, and the information was not replicated anywhere else.
For small businesses, the impact of these attacks can be devastating—not only having the potential to stop operations, but also having legal implications and a lasting impact to the company’s reputation, especially if customer or employee data is involved.
How to Defend Against Ransomware and Extortion
Preventing ransomware and extortion isn’t about just one tool—it’s about building layers of defense that work together to reduce risk and contain damage.
- Managed Detection and Response (MDR):
You might be noticing a theme here. Ransomware doesn’t usually execute instantly—it often involves initial access, privilege escalation, and lateral movement before files are encrypted. MDR solutions monitor your environment for these behaviors and can stop attackers before they hit the big red button. It’s one of the best safeguards a small business can invest in. - Backup All Critical Information:
The single most effective way to recover from a ransomware attack is to restore from a secure, offline backup. These backups should be stored separately from your day-to-day systems (e.g., in the cloud or on disconnected drives) and tested regularly to make sure they actually work. - Access Control and Account Security:
Use Multi-Factor Authentication (MFA) across all critical accounts, especially email, file storage, and admin consoles. Limit user access to only what they need, and monitor for suspicious logins or privilege escalation. - Use Secure Configurations:
Default settings often leave systems overexposed. Lock down devices and networks according to best practices, and segment your network using a firewall so that a compromise in one area doesn’t give attackers full access to everything.
#3 – Insider Threats
Not all cybersecurity threats come from the outside. Sometimes, the greatest risks are already inside your business.
Insider threats refer to risks posed by employees, contractors, or anyone with legitimate access to your systems or data. While we often think of cyberattacks as something external, insiders are uniquely positioned to cause harm—either accidentally or intentionally.
Unintentional Insider Threats
These are by far the most common. Well-meaning employees can cause a breach by:
- Clicking a phishing link that installs malware
- Sending sensitive data to the wrong person
- Using weak passwords or reusing them across systems
- Storing company files on unsecured personal devices
- Misconfiguring systems or cloud storage (e.g., leaving folders public)
These mistakes don’t come from bad intentions — they stem from a lack of awareness, poor training, or unclear policies.
It’s also important to understand that even for the best trained, well-intentioned employees – mistakes can and will happen. The field of social engineering – which attackers use to their advantage – really is a science based on human psychology.
There are hackers who specialize in social engineering and are highly skilled at infiltrating even the best-protected companies, without having to use malware or a single line of code. The largest hacker conference in the world (DEF CON) even has social engineering competitions – year after year, skilled social engineers are able to compete and exploit some of the best defended networks, on camera, publicly, in real-time for everyone to see (of course, DEF CON gets permission from the companies first!)
Intentional Insider Threats
Sometimes, the threat is deliberate. Disgruntled employees may steal data, sabotage systems, or leak sensitive information. These individuals may act out of anger, greed, or even on behalf of a competitor or foreign entity.
This is especially dangerous in small businesses, where many employees wear multiple hats and may have access to a wide range of systems and data—with little oversight.
How to Reduce Insider Threat Risk
- Use the Principle of Least Privilege (PoLP):
Only give employees access to the data and systems they need to do their job—no more. The less access a person has, the less damage they can accidentally or intentionally cause. - Strong Offboarding Procedures:
When an employee leaves—especially if under tense circumstances—immediately revoke access to all company systems, email accounts, VPNs, cloud storage, and devices. A proper offboarding checklist is critical. - Security Awareness Training:
Regularly train employees on common threats, safe data handling practices, and how to spot phishing attempts. Awareness is your first line of defense. - Activity Monitoring:
Use Managed Detection and Response (MDR) or other endpoint logging solutions such as SIEM or XDR to detect suspicious activity, like:- Accessing sensitive files at unusual hours
- Downloading large amounts of data
- Plugging in unauthorized USB devices
- This monitoring isn’t about spying—it’s about protecting your business from harmful actions, whether accidental or malicious.
A Note on Opportunistic Attacks
Many cyberattacks are not targeted at anyone in particular. Automated bots continuously scan the internet for vulnerable systems—open remote desktop ports, outdated software, misconfigured websites, and more. If your business is online (which it is), it can be targeted—just by being visible.
Understanding the Threat Landscape is Half the Battle
You don’t need to become a cybersecurity expert overnight. But having a basic understanding of the threats you face—and why attackers might target your business—helps you make smarter, more proactive decisions.
The good news? You can build strong, cost-effective defenses by focusing on fundamentals, managing your risk, and using the guidance in this course.
